It's Official, Holistics Is Now SOC2 Compliant
As a provider of business intelligence software, we understand the importance of maintaining the highest standards of security and trust. Our customers rely on us to help them make data-driven decisions, and we take this responsibility seriously. Holistics is committed to the highest standards of global security standards and privacy laws with measures in place to protect the security, confidentiality, and integrity of our customer's data.
As part of this commitment, we’re proud to announce that we recently obtained our SOC 2 Type II Report.
What Is SOC2?
SOC stands for "System and Organization Controls", and is a framework governed by the American Institute of Certified Public Accountants (AICPA). It’s the leading industry standard when it comes to security compliance and the most commonly required and accepted way to demonstrate security when conducting business in the United States. SOC2 report assures customers, partners and investors that a business has a solid baseline of security and data protection guidelines in place.
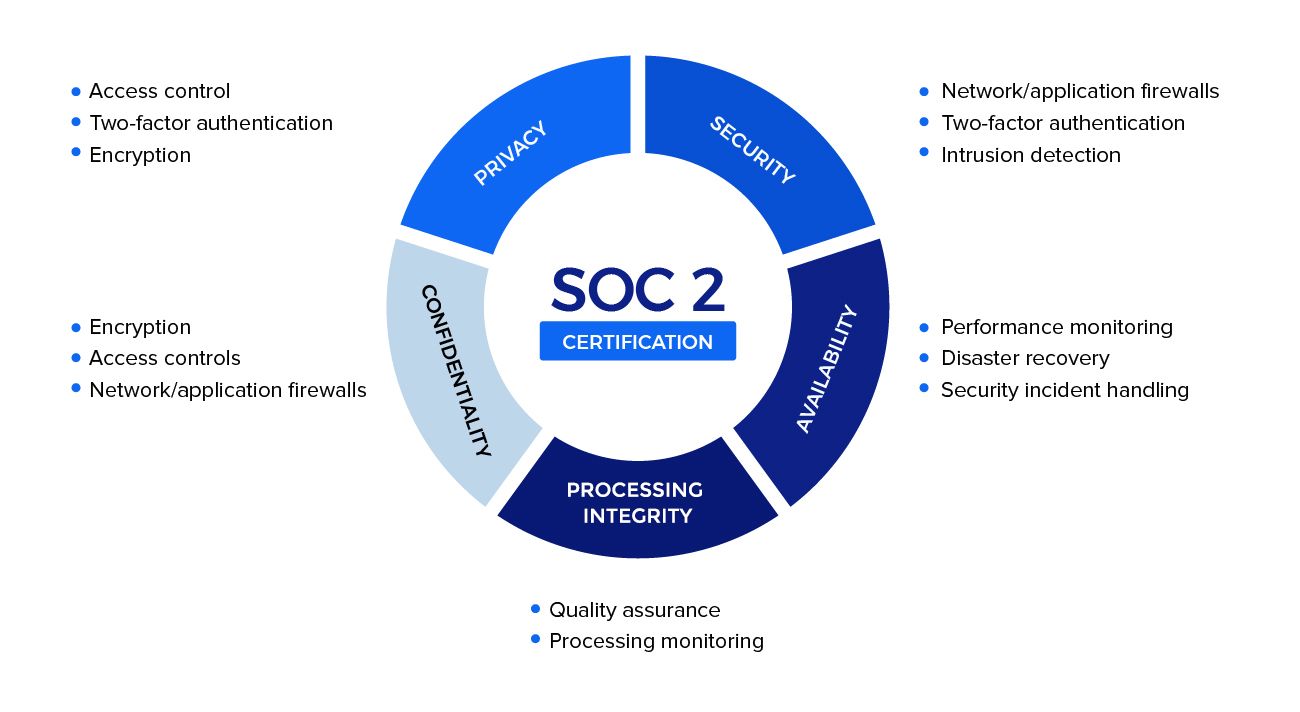
For SOC 2, AICPA has defined five Trust Services Criteria (TSC) that service organizations can choose to meet: Security, Availability, Processing Integrity, Confidentiality, and Privacy. All SOC 2 reports must cover Security. In addition to Security, service organizations like Holistics can choose to add additional criteria to their report based on what's most relevant to their business.
Once the TSCs have been chosen, the service provider must define controls to ensure that those criteria are met. For instance, to meet the Security criterion, a service provider might define a control that requires access to all sensitive internal systems to be protected by multi-factor authentication.
There are also 02 types of SOC report: Type I and Type II.
- A SOC 2 Type I report is a point-in-time report - detailing the systems, tools, and strategies you have in place for keeping customer data secure at a single point in time.
- SOC 2 Type II report, on the other hand, measures and reports on the effectiveness of a vendor’s security controls over time (generally at least 06 months). To issue a Type II report, a CPA firm not only assesses the design and implementation of a vendor's controls but also evaluates whether the controls were operating effectively over the entire audited period.
Why SOC2 Is Important
At Holistics, we chose to get a SOC 2 Type II report for two reasons:
- First, we’re committed to protecting our own networks and customer data so we can responsibly grow and remain competitive - and SOC2 offers a rigorous framework for us to do so.
- Second, we want to communicate our security practices to our customers in a more standardized and streamlined manner.
After meeting the prescribed security standards for several months and a rigorous review of our infrastructure, incident response plan, and internal policies, we’ve achieved our SOC 2 Report by partnering with Prescient Assurance, an independent auditor, and Vanta - the leading automated security platform - for continuous SOC2 compliance monitoring. We also went through thorough penetration tests, and vulnerability checks as part of this review.

Obtaining a SOC 2 Report is a critical step toward demonstrating the security of the platform for current and future customers. If you'd like to see our SOC 2 Type II report, contact us.
More about Security and Compliance at Holistics:
What's happening in the BI world?
Join 30k+ people to get insights from BI practitioners around the globe. In your inbox. Every week. Learn more
No spam, ever. We respect your email privacy. Unsubscribe anytime.
